IBIS (Accor Hotels) Door Codes Could Easily Be Hacked via Faulty Check-In Terminals
IBIS, a French brand of economy hotels, member of the Accor hotel group, was just disclosed to having unsecured check-in terminals that allowed anybody to see room assignments and access door codes.
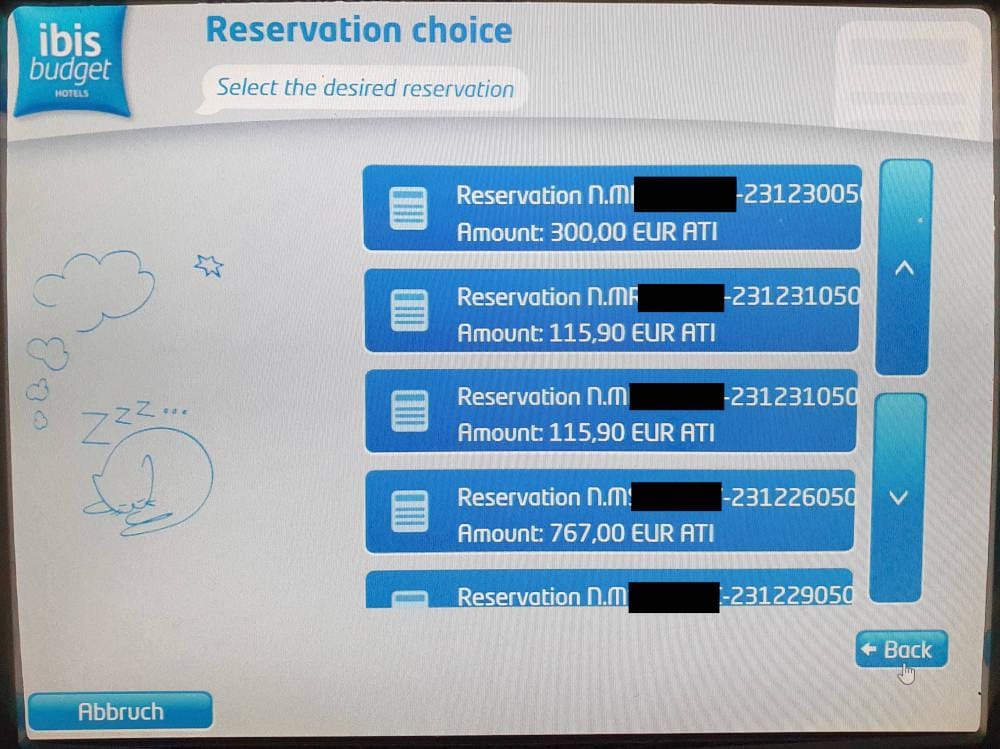
Pentagrid, which "performs technically solid security assessments of IT systems for enterprises," disclosed their findings from the past four months with Accor hotels about this security incident. In short, if you entered dashes "-" as your confirmation code it would show you a full list of all reservations including which room they are assigned, how much they paid, and crucially the access code for those rooms.
Technical Details
To use the check-in terminal's lookup function for existing hotel bookings, a guest needs to enter the booking ID. As far as observed, it is an eight-letter code. With a given booking ID, a guest can look up the room number and the room's keypad code. The keypad-code is a six-digit numeric code.
For an invalid booking ID, the terminal displays a message indicating the booking ID is not known. If a guest does not enter a booking ID but enters '——' instead, the check-in terminal lists bookings. Any other sequence of dashes is accepted if it is long enough to enable the submit button. Therefore, it is assumed that a variable length string is likely not a master code, but a bug or a not deactivated test function.
Major Privacy Breach
From Pentagrid's timeline, they took a total of just about a month to get this resolved with Accor, what is most concerning is that it took their security team awhile to actually acknowledge the security issue and fix it.

I would classify this as a major security breach, if only for the fact that someone would be able to obtain a guest's door code and enter their room at any point. We already saw a story last week about someone getting assaulted in their Marriott hotel room due to a faulty door.
It's crazy that it took two weeks for Accor to simply acknowledge the vulnerability when faced with the ultimatum of it going public after a certain amount of time after first report.
Vulnerability Fixed

Upon publication of this article, the vulnerability was patched and confirmed by Accor that it has been deployed to affected terminals. Pentagrid had some solid follow-up advice to Accor for what should be implemented as a reaction to this finding. It should not take just a booking code to retrieve a reservation from an automated terminal. I liked their suggestion of having a pin or additional verification step before displaying such sensitive information as your door code.
Final Thoughts
There's a lot to learn from security vulnerabilities. First is how a company reacts to notification of the vulnerability, I would give Accor a 5/10 for their initial response to the problem. The second is what measures are put in place to prevent it from happening again. Pentagrid did not follow up on verification of the fix, but I would assume all Accor did was make it so you can't put dashes to bring up booking codes, with no additional verification steps implemented, I would also give this response a 5/10.